“You can avoid reality, but you cannot avoid the consequences of avoiding reality.”
RMS Titanic
On April 14, 1912, the RMS Titanic hit an iceberg and sank in mid-Atlantic with the loss of 1,500 lives. What most people don’t know is what happened to her two, almost identical, sister ships and what they all had in common. Do you?
Prophetic License Plate
The automobile that Archduke Franz Ferdinand and his wife were riding in a car had a license plate “A 111118.” World War I ended four years after the assassination that started it, when the armistice (“A”) came into effect Nov. 11, 1918 (11 11 18). You can’t make this up!
Mark Twain
“Books are for people who wish they were somewhere else.”
Assassination & Armistice Both Start with “A”
The assassination of Archduke Franz Ferdinand, heir to the Austrian throne, set off World War I. What is fascinating about the automobile he and his wife were riding in at the time?
Homewrecker from Outer Space
Although the chance of a meteorite striking a house is small, of the three that have occurred in the US last century, two of the houses that were hit are in the town of Wethersfield, Connecticut. That town is only 13.1 square miles in size. The homes were struck 11 years apart, in 1971 and 1982. There were no injuries in either of those instances, but on November 30, 1954, a meteor appeared in the Alabama sky and exploded in the atmosphere just before 3:00 p.m. A chunk went through the home of Mr. & Mrs. Hodges, smashing a hole in the roof and striking Elizabeth Ann Hodges in the hip. Although there were reported close calls and some reported incidents of animals being struck prior to that incident, until then there had been no authenticated cases of a person actually being struck by a meteorite.
Abraham Lincoln
“I am a slow walker, but I never walk back.”
Meteoric
The number of documented cases of meteorites striking a house is extremely small. Only three are known to have occurred in the U.S. in the 20th century. What’s interesting about that?
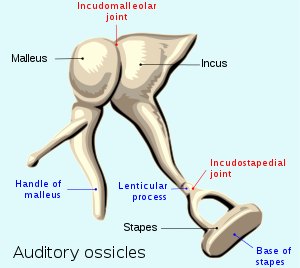
Hammer, Anvil and Stirrup
The three smallest bones in the human body, referred to as ossicles, are located in the middle ear. Individually they are named Malleus (hammer), Incus (anvil) and Stapes (stirrup).
Victor Hugo
“Not being heard is no reason for silence.”