May Queen, Wisley Crab, Foxwhelps and Lane’s Prince Albert are all species of what?
Under Water Counts!
Measured from base to peak (most of which is under water), Mauna Kea on the island of Hawaii is over 33,480 feet tall, making it the tallest mountain on Earth – taller than Mount Everest in Nepal and China. Mauna Kea is now considered dormant (scientists believe it last erupted 6,000 to 4,000 years ago).
Helen Keller
“Is there anything worse than being blind? Yes, a man with sight and no vision.”
Measured From Base to Peak
Where and what is the tallest mountain on Earth?
Bubbly, Sparkly and Heavenly
The legendary Benedictine monk who invented champagne was none other than Dom Perignon!
Margaret Mead
“If we are to achieve a richer culture, rich in contrasting values, we must recognize the whole gamut of human potentialities, and so weave a less arbitrary social fabric, one in which each diverse human gift will find a fitting place.”
I’ll Drink to That
Name the legendary Benedictine monk who invented champagne?
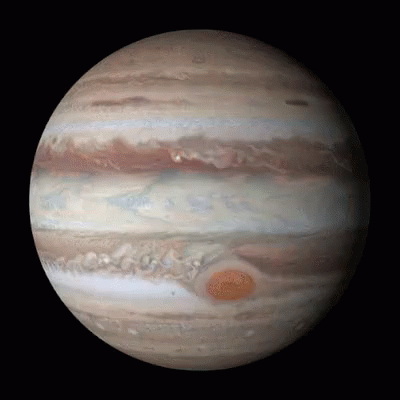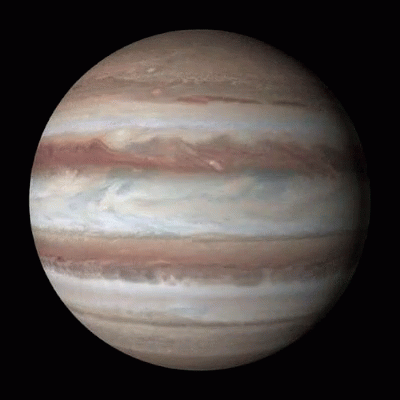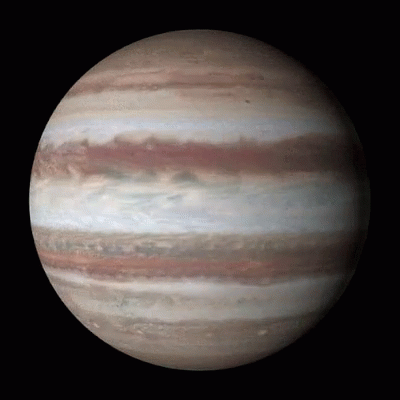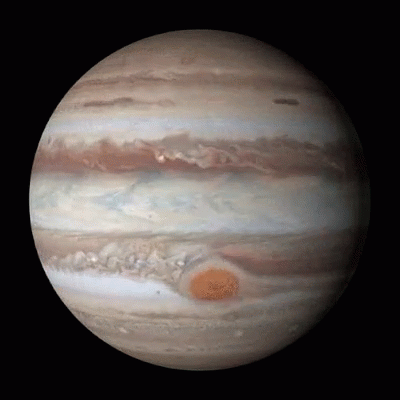
Jumping Jupiter
While Venus is the slowest planet in rotation, Jupiter, one of the largest planets in our solar system, is the fastest spinning planet, rotating on average once in just under 10 hours.
John Adams
“I always consider the settlement of America with reverence and wonder, as the opening of a grand scene and design in providence, for the illumination of the ignorant and the emancipation of the slavish part of mankind all over the earth.”
Faster Than a Speeding Planet
Venus, shown above, is the slowest rotating planet of all the major planets in our solar system – it rotates once every 243 days. But which planet spins the fastest?