Most people cannot identify the only four words in the English language which end in “dous”!!! Can you?
What’s In a Name?
The original name of the song “Silver Bells” was “Tinkle Bells” until co-composer Jay Livingston’s wife explained to him that “tinkle” had another meaning.
Ambrose Bierce (The Devil’s Dictionary)
“Litigant, noun, a person about to give up his skin for the hope of retaining his bones.”
Fake News, Troubled Celebrity Endorsements & Social Media
On Tuesday, July 24, 2018, I had the privilege of presenting a live, interactive, video-conference program and course entitled “A Perfect Storm: The Intersection of Fake News, Celebrity Endorsements & Social Media,” sponsored by Lawline.
The course was broadcast live and also recorded at Lawline’s Studio in lower Manhattan and is now available for on-demand viewing at Lawline.com. With permission, I have also posted a PDF of the PowerPoint visuals used during the presentation (although you will not be able to see the embedded videos) and you can view or download a copy for your personal use right here: A Perfect Storm: The Intersection of Fake News, Celebrity Endorsements & Social Media
As always, if you need more information, you can contact me directly (Joe Rosenbaum) or any of the Rimon attorneys with whom you regularly work.
Don’t Tinker or Tinkel With the Bells
What was the original name of the song “Silver Bells”?
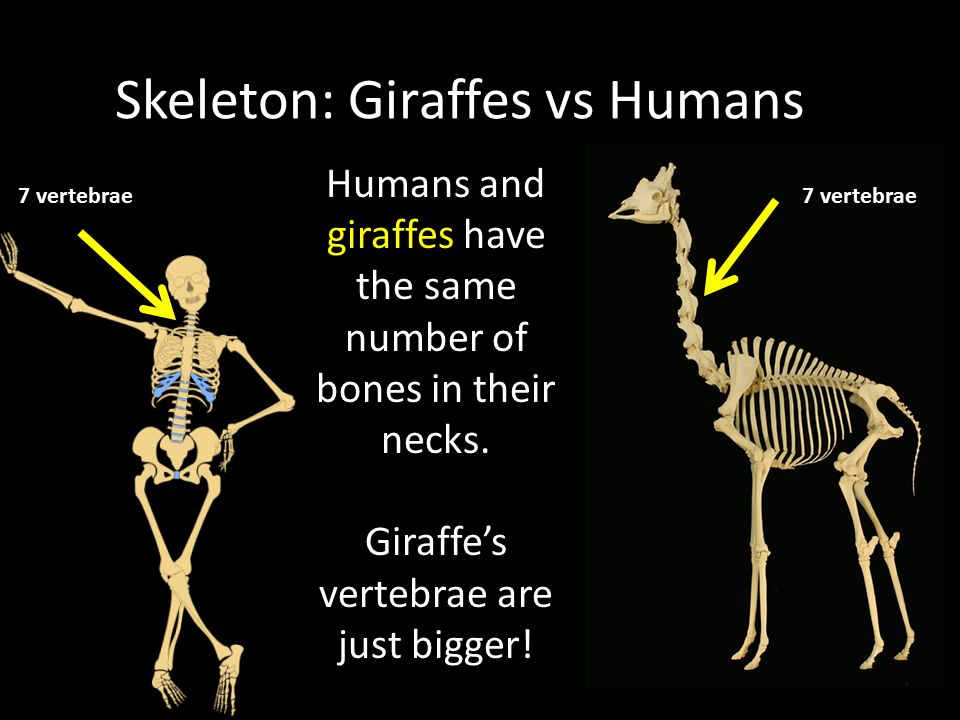
Not Long Legs – That’s For Sure
A giraffe’s long neck contains only seven elongated cervical vertebrae, the same number of vertebrae found in human necks.
Another common feature that humans share with the giraffes: each has the same amount of teeth – 32 – although giraffes have no upper front teeth. Most of their teeth are molars found in the back of their mouths.
Arthur Schopenhauer
“Talent hits a target no one else can hit; Genius hits a target no one else can see.”
Great Neck
What do humans and giraffes have in common?
Two Shooting Stars
The sequence 1531, 1607, 1682, 1758, 1835, 1910, 1986, 2062 represents the years in which Halley’s Comet appears (or in the case of 2062, will appear).
The life of Mark Twain, the pen name of Samuel Clemens, is intertwined with the comet in a unique way. Mark Twain was born (1835) and died (1910) during Halley’s comet years. What is even more remarkable is that Clemens predicted the year of his death. In 1909, he said:
“I came in with Halley’s Comet in 1835. It is coming again next year, and I expect to go out with it. It will be the greatest disappointment of my life if I don’t go out with Halley’s Comet. The Almighty has said, no doubt: ‘Now here are these two unaccountable freaks; they came in together, they must go out together.”
True to his prediction, he died of a heart attack one day after Halley’s Comet appeared at its brightest in 1910.
Alan Greenspan
“I know you think you understand what you thought I said but I’m not sure you realize that what you heard is not what I meant.”